
Thank you
Our team of industry domain experts combined with our guaranteed SLAs, our world class technology .


Get Immediate Help
Modern web applications power our daily digital interactions, from online shopping and banking to social media and enterprise systems. While these applications offer unparalleled convenience and functionality, they are also prime targets for cyberattacks. Understanding web security risks is critical for protecting your website, safeguarding user data, and ensuring business continuity.
In this blog, we’ll break down the most common web application security threats, discuss the importance of application risk assessment, and provide actionable solutions to keep your digital assets secure.

Web security risks refer to the vulnerabilities and threats that target websites, web applications, and online services. These risks arise from flaws in coding, misconfigurations, or the exploitation of modern applications’ features by cybercriminals. Left unaddressed, these vulnerabilities can lead to data breaches, financial losses, and reputational damage.

1. Cross-Site Scripting (XSS)
XSS attacks inject malicious scripts into web pages viewed by users. These scripts can steal user data, impersonate users, or spread malware.
2. SQL Injection
Attackers exploit vulnerabilities in a web application’s database by injecting malicious SQL queries. This can lead to unauthorised access to sensitive data or complete database compromise.
3. Distributed Denial of Service (DDoS)
DDoS attacks overwhelm web servers with massive traffic, making websites or applications inaccessible to legitimate users.
4. Cross-Site Request Forgery (CSRF)
CSRF tricks authenticated users into executing unwanted actions, such as transferring funds or changing account details, without their consent.
5. Insecure APIs
Modern applications rely heavily on APIs for communication. Poorly secured APIs can expose sensitive data or provide unauthorised access to backend systems.
6. Malware and Ransomware
Cybercriminals often target websites to distribute malware or lock critical systems in exchange for ransom payments.

1. Protecting Sensitive Data
Modern applications often process personal, financial, or business-critical data. Without robust security, this data is at risk of theft or misuse.
2. Ensuring Business Continuity
A cyberattack that disrupts your website or application can lead to downtime, impacting revenue and customer trust.
3. Meeting Compliance Requirements
Regulations such as GDPR and PCI DSS mandate strict security standards for handling sensitive information. Non-compliance can result in heavy fines.
4. Maintaining User Trust
Users are more likely to engage with secure websites and applications. Demonstrating strong web security builds confidence and loyalty.
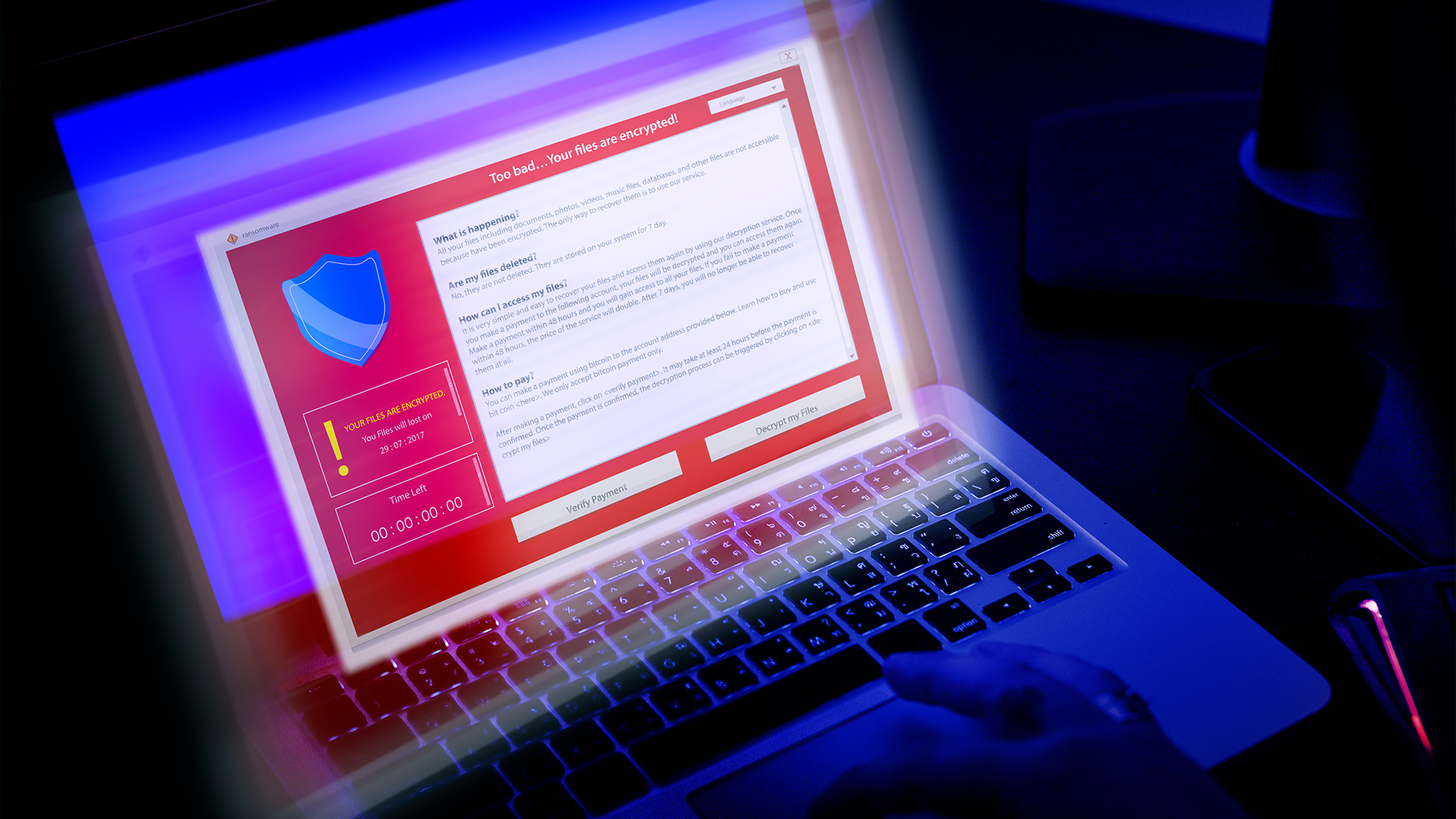
1. Regular Application Risk Assessments
Conduct periodic assessments to identify vulnerabilities in your code, infrastructure, and third-party integrations.
2. Penetration Testing
Simulate real-world attacks to uncover weaknesses before cybercriminals do.
3. Vulnerability Scanning
Automated tools can quickly scan your web applications for known vulnerabilities and recommend fixes.
4. Security Audits
Comprehensive audits provide a detailed overview of your web application’s security posture.

1. Implement Secure Coding Practices
Adopt frameworks and libraries that prevent common vulnerabilities like XSS and SQL injection.
2. Use Web Application Firewalls (WAFs)
WAFs block malicious traffic, protecting your web application from common web-based attacks.
3. Secure APIs
Use authentication protocols like OAuth and encrypt API communication to prevent unauthorised access.
4. Regular Software Updates
Keep your software, plugins, and libraries updated to patch known vulnerabilities.
5. Multi-Factor Authentication (MFA)
Add an extra layer of security for users and administrators by requiring multiple verification steps.
6. Encrypt Data
Use SSL/TLS certificates to encrypt data in transit and secure sensitive information at rest.
7. Monitor for Threats
Deploy real-time monitoring tools to detect and respond to suspicious activities promptly.
Cybersecurity as a Service (CaaS) is a cost-effective way to manage and mitigate web security risks. By outsourcing your cybersecurity needs, you gain access to:
Continuous Monitoring: Detect and respond to threats in real time.
Threat Intelligence: Stay ahead of emerging vulnerabilities and attack vectors.
Web Application Security Solutions: Tailored protections for your specific needs, including firewalls, encryption, and secure configurations.
Compliance Support: Align your web applications with industry regulations and standards.
For organisations aiming to address web security risks in modern applications, the following Microminder Cybersecurity (CS) services are especially beneficial:
1. Web Application Security Assessment
How It Helps: Identifies vulnerabilities in web applications, including coding flaws, misconfigurations, and insecure third-party integrations.
Benefit: Provides a detailed understanding of potential risks and prioritised recommendations for mitigation.
2. Penetration Testing Services
How It Helps: Simulates real-world attacks to test the resilience of web applications against threats like SQL injection, XSS, and CSRF.
Benefit: Uncovers hidden vulnerabilities and provides actionable insights to strengthen application defences.
3. Managed Detection and Response (MDR)
How It Helps: Monitors web applications continuously to detect and respond to threats in real time.
Benefit: Minimises the impact of security incidents by ensuring rapid detection and resolution.
4. Web Application Firewall (WAF) Management
How It Helps: Deploys and manages WAFs to filter and block malicious traffic targeting web applications.
Benefit: Protects against common attacks such as DDoS, SQL injection, and XSS.
5. Vulnerability Management Services
How It Helps: Conducts regular scans to identify and remediate known vulnerabilities in web applications and supporting infrastructure.
Benefit: Keeps your applications secure and up-to-date with the latest threat intelligence.
6. Security Architecture Review Services
How It Helps: Reviews the design and implementation of your web applications to identify security gaps and inefficiencies.
Benefit: Enhances the overall security framework and ensures alignment with industry best practices.
7. Cloud Security Solutions
How It Helps: Protects web applications hosted in cloud environments by securing configurations, access controls, and data encryption.
Benefit: Ensures secure cloud deployments and compliance with regulatory requirements.
8. Threat Intelligence and Hunting Services
How It Helps: Provides insights into emerging threats and actively searches for vulnerabilities within web applications.
Benefit: Enables proactive risk management and prepares your defences against new attack vectors.
9. Incident Response Retainers
How It Helps: Ensures immediate access to cybersecurity experts for containment and recovery during web application breaches.
Benefit: Reduces downtime and minimises damage caused by security incidents.
10. Compliance Gap Analysis
How It Helps: Assesses web applications for compliance with regulatory standards such as GDPR, PCI DSS, and ISO 27001.
Benefit: Ensures alignment with legal requirements, avoiding fines and reputational damage.
11. Security Orchestration, Automation, and Response (SOAR)
How It Helps: Automates incident response, vulnerability management, and compliance reporting for web applications.
Benefit: Increases efficiency and ensures rapid handling of security threats.
By leveraging these Microminder CS services, organisations can secure their modern applications, protect sensitive data, and ensure business continuity in the face of evolving cyber threats.
The landscape of web security risks is constantly evolving, making it essential for organisations to adopt proactive measures. From preventing SQL injections to securing APIs, protecting modern applications requires a combination of robust practices, advanced tools, and expert oversight.
Don’t let web security vulnerabilities compromise your business. Contact Microminder CS to secure your applications, protect sensitive data, and build trust with your users.
Don’t Let Cyber Attacks Ruin Your Business
Call
UK: +44 (0)20 3336 7200
KSA: +966 1351 81844
UAE: +971 454 01252
Contents
To keep up with innovation in IT & OT security, subscribe to our newsletter
Recent Posts
Penetration Testing | 10/11/2025
Cloud Security | 07/11/2025
Cybersecurity | 06/11/2025
What are web security risks?
Web security risks are vulnerabilities or threats targeting websites and web applications, which can lead to data breaches, unauthorised access, or operational disruptions.What are the most common types of web application attacks?
SQL Injection: Exploits vulnerabilities in database queries. Cross-Site Scripting (XSS): Injects malicious scripts into web pages. Distributed Denial of Service (DDoS): Overwhelms servers with traffic. Cross-Site Request Forgery (CSRF): Tricks users into executing unwanted actions.Why is web security important for businesses?
Web security protects sensitive customer and business data, ensures business continuity, builds trust, and helps organisations comply with regulatory requirements.How can I identify web security risks in my applications?
Conduct regular vulnerability assessments. Perform penetration testing. Use security monitoring tools for real-time insights. Engage in periodic security audits.What is a Web Application Firewall (WAF), and how does it help?
A WAF is a security tool that filters, monitors, and blocks malicious traffic targeting web applications, protecting against common threats like SQL injection and XSS.